To keep up with the massive influx of data and the increased demands on the network for speed and agility, networking professionals are learning to broker, connect, build, and govern their networks not only in the data center, but also across a vast cloud landscape.
Cisco ACI was built to simplify the IT infrastructure and operations by automating the network, providing pervasive security, and helping accelerate businesses to move to a cloud or multicloud environment.
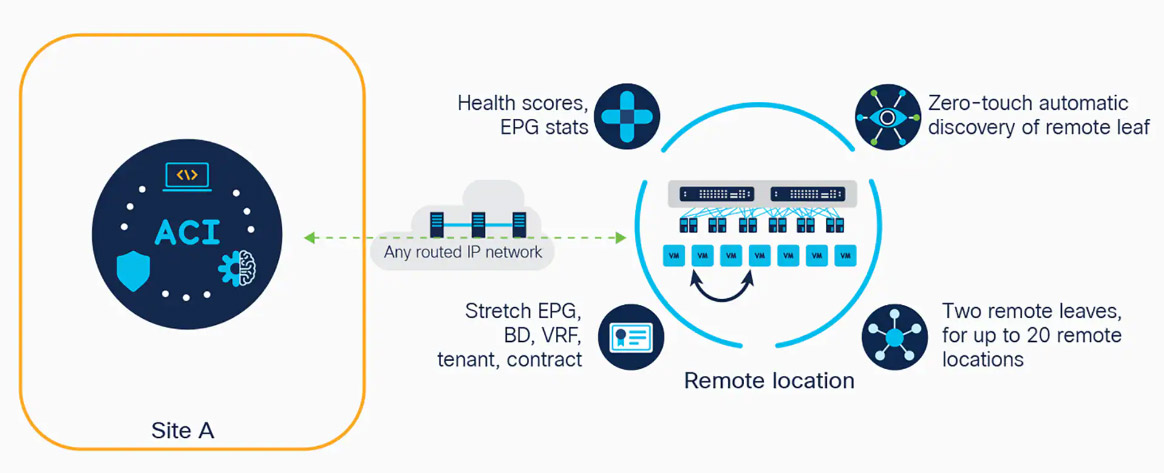
With Cisco ACI, customers can manage complexity, maximize business benefits, and deploy workloads in any location, small and large, on premises and remote locations, in private and public clouds, satellite data centers, and 5G-enabled telecom edges.
The main benefits of Cisco ACI include the following :
Accelerate network operations :
Cisco ACI provides a flexible and yet highly available network that allows agile application deployment within a site, across sites, and across global data centers while removing the need for complex Data Center Interconnect (DCI) infrastructure
â— Operational simplicity, with common policy, management, and operation models across application, network, and security resources
â— Centralized network management and visibility with full automation and real-time network health monitoring
â— Seamless integration of underlay and overlay networks
â— Open northbound APIs to provide flexibility for DevOps teams and ecosystem partner integration
â— A cloud-ready SDN solution
â— Common platform for managing physical and virtual environments
â— Automation of IT workflows and application deployment agility
Securely expand to multicloud :
â— Create business continuity and provide disaster recovery
â— Inherent security with a zero-trust allow-list model and innovative features in policy enforcement, microsegmentation, and analytics
â— Integrated security with Cisco security products and ecosystem partners
â— Consistent security posture at scale across a multicloud environment
Deliver superior application experience :
â— Single policy and seamless connectivity across any data center and public cloud
â— Through any hypervisor, for any workload, at any location, using any cloud
â— Cloud automation enabled by integration with VMware vRealize, Azure Pack, OpenStack, OpenShift, Kubernetes, and Cisco UCS® Director
â— Open APIs and a programmable SDN fabric, with 65+ ecosystem partners