| Parameters of Comparison |
Cisco FTD | Cisco ASA |
|---|---|---|
| VPN Support | Not Available | Available |
| Configuration | More of a software-based firewall | Either a Stateful Packet Inspection firewall or a Network Address Translation firewall |
| Performance | Top-Notch Performance | Low Quality Performance |
| Time Consumption | Less Time Consuming | High Time Consuming |
| Affordability | Highly-Affordable | Less-Affordable |
| Old | New |
|---|---|
| Sourcefire | Cisco |
| Sourcefire Defense Center | FireSIGHT Management Center (FMC or FSMC) |
| Sensor | Device or Managed Device |
| Defense Center (DC) | FireSIGHT Management Center |
| Sourcefire 3D System | FireSIGHT System |
| Sourcefire Managed Device | Managed Device |
Feature |
Reason |
Resource |
|---|---|---|
|
AMP for Networks |
Malware cloud lookups. |
cloud-sa.amp.sourcefire.com cloud-sa.eu.amp.sourcefire.com cloud-sa.apjc.amp.sourcefire.com cloud-sa-589592150.us-east-1. |
|
Download signature updates for file preclassification and local malware analysis. |
updates.vrt.sourcefire.com amp.updates.vrt.sourcefire.com |
|
|
Submit files for dynamic analysis (managed devices). Query for dynamic analysis results (FMC). |
panacea.threatgrid.com |
|
|
AMP for Endpoints integration |
Receive malware events detected by AMP for Endpoints from the AMP cloud. |
api.amp.sourcefire.com api.eu.amp.sourcefire.com api.apjc.amp.sourcefire.com export.amp.sourcefire.com export.eu.amp.sourcefire.com export.apjc.amp.sourcefire.com |
|
Security Intelligence |
Download Security Intelligence feeds. |
intelligence.sourcefire.com |
|
URL filtering |
Download URL category and reputation data. Manually query URL category and reputation data. Query for uncategorized URLs. |
database.brightcloud.com service.brightcloud.com |
|
System updates |
Download updates directly from Cisco to the appliance:
|
cisco.com sourcefire.com |
|
Time synchronization |
Synchronize time in your deployment. Not supported with a proxy server. |
0.sourcefire.pool.ntp.org 1.sourcefire.pool.ntp.org 2.sourcefire.pool.ntp.org 3.sourcefire.pool.ntp.org |
|
RSS feeds |
Display the Cisco Threat Research Blog on the dashboard. |
blogs.cisco.com/talos cloud.google.com |
|
Whois |
Request whois information for an external host. Not supported with a proxy server. |
The whois client tries to guess the right server to query. If it cannot guess, it uses:
|
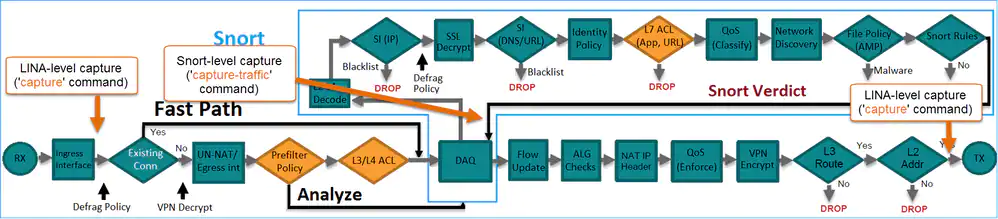
Sources : Cisco, and more..