! " # $ % & ' ( ) * + , - . / : ; < = > ? @ [ \ ] ^ _ ` { | } ~Capabilities |
Microsoft Intune |
SCCM |
|---|---|---|
|
Platform |
|
|
|
Microsoft Windows |
Yes |
Yes |
|
Microsoft Windows Server |
No |
Yes |
|
Windows Phone |
Yes |
Windows 10 only |
|
iOS |
Yes |
No |
|
Windows RT |
Yes |
No |
|
Android |
Yes |
No |
|
Compliance Settings |
|
|
|
Deploy and customize Windows PC device configuration settings (e.g., WMI, registry) |
No |
Yes |
|
Deploy configuration settings to mobile devices. |
Yes |
No |
|
Deployment |
|
|
|
Deploy apps to devices and Windows PCs |
Yes |
Yes |
|
Deploy Windows operating systems |
No |
Yes |
|
Security and Privacy |
|
|
|
Manage Windows software updates |
Yes |
Yes |
|
Administration and Reporting |
|
|
|
Monitor and report on how often software is being used with software metering |
No |
Yes |
|
Hardware and software inventory |
Yes |
Yes |
|
Use role-based administration and reporting to control who has access to product capabilities |
No |
Yes |
|
Data Protection for mobile devices |
|
|
|
Deploy security settings to mobile devices |
Yes |
Yes |
|
Remote lock |
Yes |
Yes |
|
Company resource access |
|
|
|
Email profiles |
Yes |
Yes |
|
Mobile application management |
Yes |
Yes |
|
Manage access to Exchange email and SharePoint with conditional access |
Yes |
Yes |
|
Managed Internet browser policy |
Yes |
Yes |
| Plan | Basic Mobility and Security | Microsoft Intune |
|---|---|---|
| Microsoft 365 Apps | Yes | No |
| Microsoft 365 Business Basic | Yes | No |
| Microsoft 365 Business Standard | Yes | No |
| Office 365 E1 | Yes | No |
| Office 365 E3 | Yes | No |
| Office 365 E5 | Yes | No |
| Microsoft 365 Business Premium | Yes | Yes |
| Microsoft 365 Firstline 3 | Yes | Yes |
| Microsoft 365 Enterprise E3 | Yes | Yes |
| Microsoft 365 Enterprise E5 | Yes | Yes |
| Microsoft 365 Education A1 | Yes | Yes |
| Microsoft 365 Education A3 | Yes | Yes |
| Microsoft 365 Education A5 | Yes | Yes |
| Microsoft Intune | No | Yes |
| Enterprise Mobility & Security E3 | No | Yes |
| Enterprise Mobility & Security E5 | No | Yes |
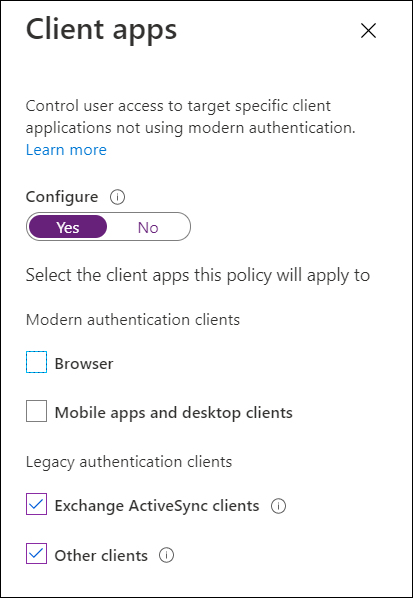
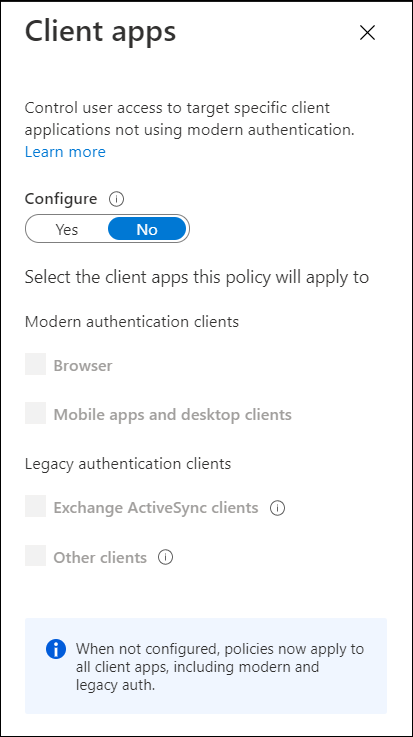
Devices > Windows > Configuration profiles and click on "+ Create profile". Select "Windows 10 and later" as the platform and "Script" as the profile type. Configure the settings for the script, including the name of the script, the script content, and any parameters that need to be passed to the script.
3. Assign the script configuration policy : In the Assignments section of the policy, choose the group of devices or users that you want to apply the script to. You can also set a specific schedule for when the script should be run.Apps > All apps > "+ Add" and choose the app package type you want to add. Upload the app package, and then fill out the necessary fields, such as app name, description, and publisher. You can also set any dependencies and deployment settings for the app.