ln [original filename] [link name]?ln -s [original filename] [link name]?/dev/null (a special file that discards data written to it), /dev/random and /dev/urandom (special files used for generating random data), and /proc (a virtual file system that provides information about processes and system resources).rm –r* is used to erase all files in the current directory including all its sub-directories. rm is used for deleting files, but with the addition of option -r it erases all files in directories and subdirectories, and finally, an asterisk represents all entries.
|
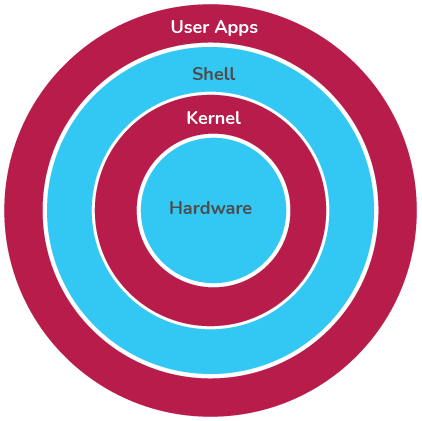
Shell |
Indicators |
|---|---|
|
Bourne Shell |
|
|
C Shell |
|
|
Bourne Again shell |
|
|
Enhanced C shell |
|
|
Z Shell |
|
|
Korn Shell |
|
<', '>', and '|'.$who | sort | lpr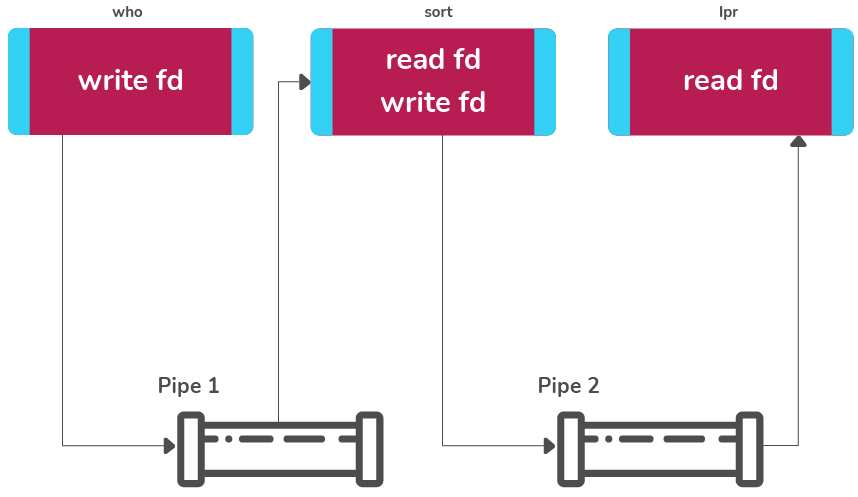
egrep is an extended version of grep, in addition to searching using regular expressions, egrep can use extended regular expressions for searching.$ ls | grep '.env|.json'?$ ls | egrep '.env|.json'?.env’ or ‘.json’ since ‘|’ this will be considered as a metacharacter. command - (options) argument1 argument2..?*.txt matches all files with a ".txt" extension.file* matches all files whose names start with "file".file?.txt matches files like "file1.txt", "fileA.txt", etc.[abc] matches any one of the characters 'a', 'b', or 'c'.[0-9] matches any digit from 0 to 9.[!0-9] matches any character that is not a digit.{file1,file2,file3}.txt matches "file1.txt", "file2.txt", and "file3.txt".{1..5} matches the numbers 1, 2, 3, 4, and 5.ls, cp, mv, rm, and grep to perform file operations, file matching, and text processing. They provide a powerful and flexible way to specify patterns and perform operations on multiple files or text strings at once, saving time and effort for users working in the command line. fork(). The main process is called the parent process and new process is called child process. The parent gets the child process is returned and the child gets 0. The returned values are used to check which process which code executed.Cmp compares the two given files, byte by byte and displays the first mismatch.Diff displays the changes that need to be made in order to make both the files identical.
chmod changes the permission set of the file.chown changes the ownership of the file.chgrp changes the group of the file.
–v option echoes each command before arguments and variables have been substituted for; the –x option echoes the commands after substitution has taken place.
(User permission) – (Group permission) – (Other permission)r – Reading permissionw – Writing permissionx – Execution permission getppid() retrieves the Parent Process ID?getpid() retrieves the Process IDgetuid() retrieves the User IDgeteuid() retrieves the Effective User ID -l, which is normally used in listing command like ls, is used to show files in a long format, one file per line. Long format refers to additional information that is associated with the file, such as ownership, permissions, data, and filesize.
| ls -a | In Linux, hidden files start with. (dot) Symbol and they are not visible in the regular directory. The (ls -a) command will enlist the whole list of the current directory including the hidden files. |
| ls -l | It will show the list in a long list format. |
| ls -lh | This command will show you the file sizes in human readable format. Size of the file is tough to read when displayed regarding a byte. The (ls -lh)command will give you the data regarding Mb, Gb, Tb, etc. |
| ls -lhS | If you want to display your files in descending order (highest at the top) according to their size, then you can use (ls -lhS) command. |
| ls -l - -block-size=[SIZE] | It is used to display the files in a specific size format. Here, in [SIZE] you can assign size according to your requirement. |
| ls -d */ | It is used to display only sub directories. |
| ls -g or ls -lG | With this, you can exclude column of group information and owner. |
| ls -n | It is used to print group ID and owner ID instead of their names. |
| ls --color=[Value] | This command is used to print list as colored or discolored. |
| ls -li | This command prints the index number if the file in the first column. |
| ls -p | It is used to identify the directory easily by marking the directories with a slash (/) line sign. |
| ls -R | It will display the content of the sub-directories also. |
| ls -lX | It will group the files with the same extensions together in the list. |
| ls -lt | It will sort the list by displaying a recently modified file at the top. |
| ls ~ | It gives the contents of the home directory. |
| ls ../ | It gives the contents of the parent directory. |
| ls --version | It checks the version of ls command. |
.(dot) before the file name. These files do not show up in the traditional file manager..profile.kshrc.rhosts.cshrc $ ls -l /home/sroy8091
-rwxr-xr-- 1 sroy8091 users 1024 Feb 23 00:10 myfile
drwxr-xr--- 1 sroy8091 users 1024 Feb 23 00:10 mydir?$ ls -l testfile
-rwxrwxr-- 1 sroy8091 users 1024 Feb 23 00:10 testfile
$ chmod o+wx testfile
$ ls -l testfile
-rwxrwxrwx 1 sroy8091 users 1024 Feb 23 00:10 testfile?kill PID
nohup” is a special command that is available to run a process in the background. The process starts with ‘nohup’ command and does not terminate even if the user started to log off from the system.
fork() system call is incurred for protection fault.
set path = [directory path]” command.
$ wc filename?df" command in UNIX. For example "df -h ." will list how full your current drive is. This is part of anyone day to day activity so I think this Unix Interview question will be to check anyone who claims to working in UNIX but not really working on it.
ps –ef command and we are wondering which process is holding the file.ps -ef will omit process with very long command line while ps -auxwww will list those process as well.
| Absolute Path | Relative Path |
| It is known as the absolute path | It is known as the non-absolute path |
| It refers to a specific location in a file system without denoting the current directory. | It refers to a location denoting the current directory |
| It contains the complete address of a file location. | It contains the partial address of a file location. |
| This path doesn’t change if we change the current directory | This path changes if we change the current directory |
rm { file name }?rm abc. txt?gzip command in Unix-like operating systems is used for file compression and decompression. It is commonly used to reduce the size of files, making them easier to store, transfer, and archive. The name "gzip" stands for "GNU zip," indicating its association with the GNU project.gzip command :gzip command replaces the original file with a compressed version, appending the ".gz" extension to the filename. It uses the DEFLATE compression algorithm to compress data efficiently, typically achieving significant reductions in file size, especially for text-based files.gzip [options] filename?gzip example.txt?gzip command can also be used to decompress compressed files created with gzip or compatible compression programs. It restores the original uncompressed file, removing the ".gz" extension from the filename.gzip -d filename.gz?gzip -d example.txt.gz?gzip command supports various options and flags to customize its behavior, including options to specify compression level (-1 for fastest compression, -9 for best compression), preserve file attributes (-c for output to standard output, -k to keep the original file), force compression or decompression (-f), and more. You can see the full list of options by running gzip --help.gzip -9 example.txt # Compress with the highest compression level?gzip command is a versatile and efficient tool for compressing and decompressing files in Unix-like environments, helping users save disk space, reduce bandwidth usage, and simplify file management tasks. file/directory and a way to access it within the hierarchy of directories. There are basically two types of pathnames that are used in Unix.file/ directory from the very start of the actual file system(root directory)./usr/local/Cellar the the relative path for bin is ./mysql/bin alias gco='git checkout -b'?$grep pattern file(s)-v : prints a line that does not match the pattern.-n : print matched line and line number.-l : print file names with matching lines.-c : prints only count the matching lines.-i : matches either uppercase or lowercase. $’ character.set’ command is used.unset’ command is used. redirection’ and ‘cat’ commands, allows setting a variable to the content of the file.nslookup command is used to query internet domain name servers which can be used to find hostname from an IP address and for reverse lookup also, Similarly host command can also be used.
| Command | Description |
|---|---|
| cat filename | Displays contents of the file |
| cp source destination | Used to copy source file into the destination |
| mv old name new name | Move/rename and old name to the new name |
| rm filename | Remove/delete filename |
| Touch filename | Changing modification time |
| In [-s] old name new name | Creates soft link on old name |
| Is –F | Displays information about file type |
Chmod [options] mode filename.-R : recursively change the permission of the file or directory.-v : verbose, i.e. output a diagnostic for every file processed.-c : report only when the change is made.Kill() system call is used to send signals to any processes.–s target link_nametarget’link_name.