If you got an email from yourself with ransom threats, the first step is to stop and collect yourself. We’ve already touched on how easy it is to spoof an email. Panicking is playing into the attacker’s hands. What you’ll need to do then is to investigate the email header and check for the IP addresses, SPF, DMARC, DKIM validations. This will clear out whether the email came from your own account. If the validation fails, there’s nothing to worry about. If the email truly came from your own inbox, you need to act fast and take all precautions to protect your email and your identity.
Identifying email spoofing : Incidentally, it’s incredibly easy to identify email spoofing. Aside from the obvious red flags, you only need to look at the full email header. It contains all the critical components of every email: From, To, Date and Subject. Also, there will be metadata on how the email was routed to you and where it came from. Most likely, it will also contain the verification results your internet service provider used to check if the sender’s server had the proper authorization to send emails using that domain.
How you check this data heavily depends on the service you’re using and will only work on a desktop. For Gmail, you’ll need to click three vertical dots next to the reply button and select “Show Original” from a drop-down list. For other services that you may be using, you can check
this list.
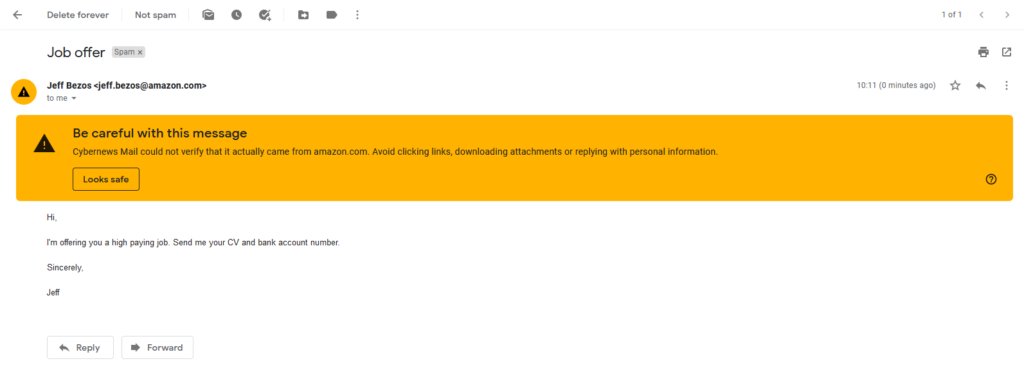
Here’s an example of a spoofed email that I sent to myself pretending to be a billionaire. In this case, the email filter caught it labeling it as spam, so it didn’t appear in my primary mailbox. I had to find it in the spam folder. Big yellow warning aside, you’ve got to admit, it looks pretty realistic.
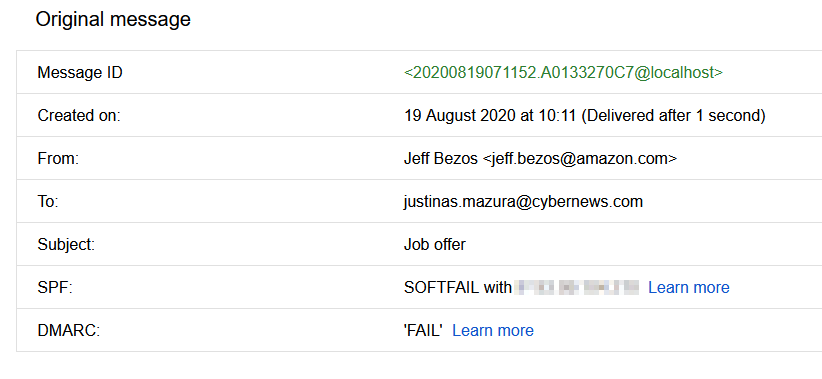
Suppose I would have picked a lower-profile domain of a lesser-known company with fewer methods to verify. Well, there is still a lot that you can check. If you go to “Show Original“, you can see that SPF is indicated as SOFTFAIL, and DMARC is indicated as FAIL. This is enough to call out the email as spoofed. Some poorly maintained domains do not keep their SPF records up to date, failing validation.
If you want to go deeper down the rabbit hole, at the code level, you’ll see that Received: from, and Received-SPF domains do not match, as well as the IP addresses. This is a clear example of email spoofing. Remember, if IP addresses don’t match and SPF validation fails, this isn’t a genuine email. It doesn’t also hurt to check whether the Return-Path is the same as the sender’s email address.
Source : Cybernews