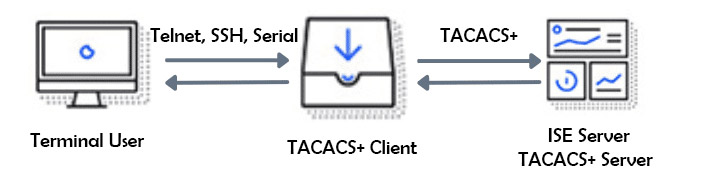
As mentioned earlier, the TACACS+ protocol is used between the Cisco ISE server and the network device (AAA or TACACS+ client). Keep in mind that Cisco ISE can separate Authentication, Authorization, and Accounting requests.
* When a network device administrator (Terminal User) attempts to log into a device (AAA/TACACS+ client) via Telnet or SSH, the device instantly queries the Cisco ISE (AAA and TACACS+ server) via the TACACS protocol to validate the authentication.
* The Cisco ISE server, in turn, uses policy authentication sets to either respond with an “accept” or “reject” to the network device.
* If the user is granted access > the network device queries the Cisco ISE using TACACS+ for authorization The ISE Server checks for authorization policy rules for TACACS+ results, such as command sets and shell profiles.
* The user is then provided with a set of commands or shell profiles to perform certain actions on the networking device.
* Finally, the Cisco ISE Server provides accounting by logging the activity and providing reports so that an ISE administrator can produce detailed audits.